
Sophos Cloud Native Security
Complete cloud security coverage across multiple environments, workloads, and identities.
Delivering Complete Multi-Cloud Security Coverage Across Environments, Workloads, and Identities
Our cloud-managed Wi-Fi provides the best AP support, scalability and a single pane of glass via Sophos Central
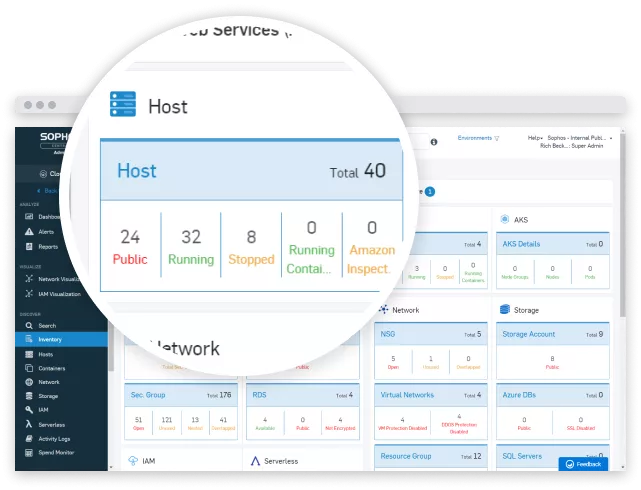
Visibility, Governance, and Compliance
View your multi-cloud environments to detect and remediate security risks, reduce your attack surface, and maintain compliance.
- Increase efficiency by monitoring posture across AWS, Azure, GCP, Kubernetes, Infrastructure as Code, and Docker Hub environments in a single console.
- See it all: Asset inventories, network visualizations, cloud spend, and configuration risk.
- Automate compliance assessments and save weeks of effort with audit-ready reports.
- Reduce risk without losing DevOps speed with Infrastructure as Code and container image security.
- Prioritize resources with risk-assessed and color-coded alerts.
- Provide detailed alerts and guided remediation to help your teams build their cloud security skills.
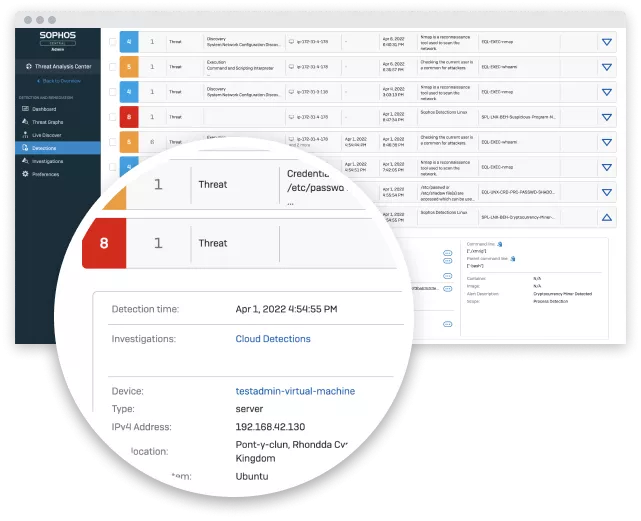
Protect Cloud Workloads and Data
Protect your infrastructure and data now and as it evolves with flexible host and container workload security.
- Get performance and uptime with lightweight Linux and Windows host protection via agent or API for Linux.
- Protect it all: Cloud, data center, host, container, Windows, and Linux.
- Identify sophisticated Linux security incidents at runtime without deploying a kernel module.
- Secure your Windows hosts and remote workers against ransomware, exploits, and never-before-seen threats.
- Manage applications, lock down configurations, and monitor changes to your critical Windows system files.
- Utilize XDR to streamline threat investigations and response and prioritize and connect events.
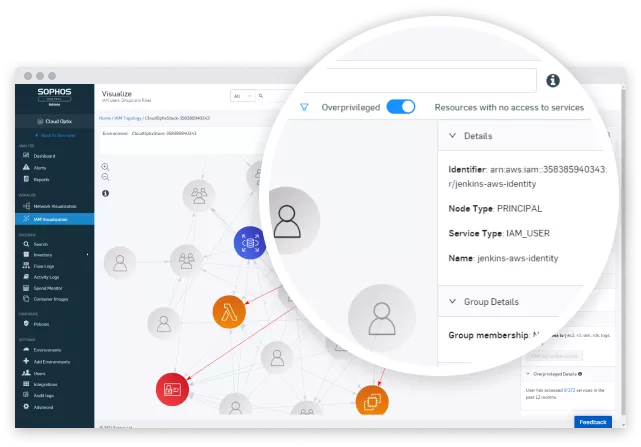
Enforce Least Privilege
Implement least privilege across your multi-cloud environments and manage your identities before they’re exploited.
- Ensure all identities only perform actions that are required for their tasks and nothing more.
- Visualize complex, interwoven IAM roles to quickly highlight and prevent over-privileged IAM roles.
- Pinpoint unusual user access patterns and locations to identify credential misuse or theft.
- Utilize SophosAI to connect disparate high-risk anomalies in user behavior to prevent breaches.

Request Sophos Cloud Native Security Price
Contact sophos distributor in Egypt